What Is Shadow IT in Cloud Computing?
Definition of Shadow IT is its utilization of related equipment or programming by a division or individual without the information on the IT or security bunch inside the association. It can incorporate cloud administrations, programming, and equipment.
The primary zone of concern today is the quick reception of cloud-based administrations. The development of shadow IT solutions has quickened with the consumerization of data innovation. Clients have become happy with downloading and utilizing applications and administrations from the cloud to help them work.
How Shadow IT Impacts the Enterprises?
The use of applications without the approval of the IT team creates room for serious information security risks as the organizations lose control over their enterprise data which is residing in the cloud. There is no control on the following:
- Applications used by users within the organization
- Enterprise data being uploaded to unauthorized or un-secure portals
- Installation of unauthorized apps
- Access to un-secure apps
- Programs downloaded from unauthorized or un-secure portals
These can become gateways for data loss for the enterprises giving unauthorized access to third parties to their enterprise data. For e.g, data loss and downtime can occur if the software is downloaded or a tool is run, which might have a crypto locker and starts to encrypt files across the file server.
The Hidden Cost of Shadow IT
For independent companies, shadow IT costs are generally gotten from free cloud administrations and additionally record the board programming. Commonly we’ll see organizations use arrangements like File Server, nearby work area stockpiling, DropBox, Sharepoint, or potentially Google Drive. Nobody realizes where documents are put away and can take them valuable additional minutes every day to look through every arrangement executed.
We call these manual workarounds shadow IT costs. It’s the concealed expense of helpless arrangement execution. Workers utilize what’s generally helpful for them while disregarding everyone’s benefit from the organization. Also, that is expensive.
Shadow IT Challenges
- Data loss- When unapproved programming runs inside the system, there’s consistently a danger of losing information that is basic for the organization. From one viewpoint, there’s a sensible possibility that there is no support of these applications and that workers who use them haven’t considered making an appropriate recuperation methodology. Along these lines, if something occurs, important information might be lost, and there will be practically zero possibility of restoring it.
- Lack of security- The absence of transparency and command over system components are the primary cyber security dangers of utilizing shadow IT. They make various insecure areas that programmers may use to trade off a framework and gather or take delicate business data. Also, since the IT division doesn’t manage unsanctioned programming and applications, they, for the most part, have loads of unpatched blunders and weaknesses.
- Inefficiencies- Changes to equipment and programming inside the shadow IT probably won’t experience any testing. Legitimately executed frameworks and arrangements may quicken singular procedures, however on the other hand, a progression of different business procedures may slow down. In the most dreadful outcome imaginable, this could imply that business-basic IT assets are not, at this point, accessible. Moreover, shadow IT involves a twofold organization and support exertion of frameworks and programming – if any upkeep inside the shadow IT condition happens by any stretch of the imagination.
- Compliance- Utilizing shadow IT, forms are regularly settled in the pro divisions that abuse the organization’s existing consistent rules. Also, the presentation and utilization of shadow IT are now a violation of the standard organization’s consistency rules. For some organizations, such a key penetrate of consistent rules can compromise their reality.
- Security shortcomings- Shadow IT introduces security holes with an organization. Since the IT division hasn’t reviewed it, shadow IT doesn’t experience the identical security strategies from other supported advancements. While some unsupported SaaS applications appear weak, others may support sharing delicate information between gatherings or recording calls for record administrations. IT staff has to realize what applications are used and how they may put your organization in danger of information penetrates and different liabilities.
Managing Shadow IT Threats:
- Scope of Shadow IT: As per statistics, the use of Shadow IT in an organization ranges between 30- 60%, and the survey clearly depicts a growing trend in them. Firstly, organizations must conduct a survey to know the presence of Shadow IT within their organization. It is advisable to keep track of what users are connecting to, and for how long are they are using it. The easiest way to know the presence of Shadow IT is through regular monitoring of networks and scanning unknown devices. This process helps in gathering more information about the new and unknown devices on the network.
- Risk evaluation: Not every device and software network is prone to risks. The first step in the process of evaluating this issue is to first identify and address the high-risk services in the network. It is essential to take timely actions and blocking the access of certain authorized users on any foreign device. The information technology team of any organization must conduct a thorough regulatory and examination process to identify such threats and protect the network by taking stringent actions against such authorized users.
- Technology and Guidelines: It is crucial to resolve the challenges faced by organizations due to Shadow IT. The IT experts can share all the authorized and approved applications with the users to prevent any sort of data breach. It purely depends on the organizations to approve any device or technology after thorough authentication and verification. No company can compromise with its data security and privacy; hence it is the responsibility of the organization to encourage its users to access only authorized and approved technology, application, or device.
- Restriction on third-party apps: Companies these days need to be ahead of time in operating their business. Organizations can always restrict certain third-party apps like Dropbox, SharePoint, and a few others, which lead to cyber threats. Furthermore, companies can also layout stringent IT policies for their employees to prevent them from accessing any third-party applications or suspicious application on the cloud. Organizations these days have set up an internal IT auditing team that keeps a regular check on all the applications and the users accessing it.
- Flexibility to users: In this fast-paced world, each one of us wants to access the data on any available device. Organizations can provide secure and easy to access data networks to their employees, which not just reduces the risk of data threats but also encourages flexible access to information to authorized users. With the help of a mobile management platform or strict cyber policies, an organization can always monitor the devices on which their employees are accessing information and take necessary actions in case data threats or policy violations.
Advantages of Shadow IT
- Scope for employees- Application improvement has, for quite some time, been a torment point in numerous organizations. It’s one motivation behind why clients went to Shadow IT in any case. They became weary of looking out for new applications from IT and chose to assume control over issues. They discover apparatuses that either address their concerns or let them manufacture their applications.
- Solution-oriented- At the point when business clients demand methods from IT, the subtleties frequently lose all sense of direction in interpretation. Thus, the completed item isn’t actually what the client mentioned. Shadow IT helps address this issue, as it takes out the danger of miscommunication. At the point when the clients are the ones discovering/building their answers, they find out patterns that better line up with their objectives.
- Improves productivity- Workers go to Shadow IT when they can’t get the arrangements they need or get around limitations set up by the business. In numerous organizations, the IT office is seen as a deterrent as opposed to an accomplice. Or then again, exacting corporate arrangements make it challenging to achieve quite a bit of anything. When you grasp Shadow IT, you can give representatives the devices they require for their regular undertakings. Accordingly, they invest less energy searching for workarounds and additional time completing things.
- Eases IT workload- In many organizations, the IT division is exhausted. They keep the innovation running, bolster the business, and are continually extinguishing fires. Dealing with end client demands for new arrangements adds to their rundown of undertakings. At the point when Shadow IT is grasped, end clients approach an assortment of pre-endorsed arrangements or the instruments to make their own. It expels a weight from the IT office and lets them center around other, strategic undertakings.
Shadow IT and Its Best Practices
- Analyze- While it’s critical to change conventional IT dynamic procedures, it’s considerably progressively essential to do it in a savvy way. Associations should start a straightforward investigation of received SaaS applications. It’s exceptionally imperative to comprehend if a particular application is reasonable for your organization. Your employees can utilize trial applications; however, they require checking and research. After introductory investigates, you can pick whether an application is permitted, limited, or shared.
- Development strategy- Leaders who take part in shadow application advancement might be working with a hazardous information shortage. Assessing the progress of an application requires decent working information on programming engineering, plan designs, and the most recent secure programming methods – abilities, not many nontechnical administrators have. Not staying aware of the most current secure programming methods could prompt security issues that bring about lost delicate information.
- Cloud security provider- Innovation supervisors may accept that cloud suppliers consequently handle the entirety of their security needs out of the container. If the Shadow IT purchaser doesn’t require some investment to figure out how to utilize cloud security highlights, it could leave the cloud condition helpless against assault. Security is a mutual duty, and cloud purchasers must instruct themselves and their groups on the best way to safely utilize the new foundation.
- Data storage- Employees can undoubtedly send documents to their own cloud space to take a shot at them at home. However, they may neglect to make even the most fundamental security precautionary measures when utilizing these administrations. Programmers can crush secret phrase insurances, and access decoded recognizable data (PII) and ensured wellbeing data (PHI). Managers can’t screen or review the progression of this information, implying that they can’t be sure which information is undermined in case of penetration. Moreover, the executive can’t know whether a representative’s very own record is penetrated.
Shadow IT Statistics
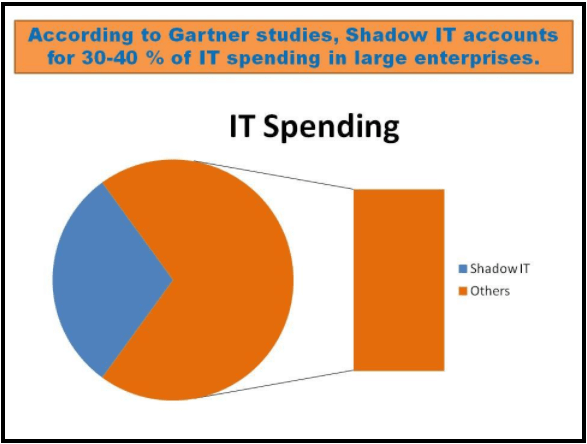
- As per Gartner studies, shadow IT accounts for 30-40% of IT spending in large enterprises.
- As per Cisco findings, around 83% of the support staff admits of using unsanctioned apps in the enterprise cloud environment.
- EMC’s recent study suggests data loss & downtime costing around $1.7 Trillion every year.
These alarming statistics surely indicate that there is a massive impact of Shadow IT. Still even this is an understatement in terms of the entire shadow IT ecosystem. Many businesses even cripple when sensitive information gets leaked. It is a real big problem, and highly complicated.
Shadow IT: Emergence and Threat
Shadow IT can occur almost naturally and even can be with undeceiving intentions. It happens just when any technology solution seems useful and safe, and that is very easily accessible that lures the employees to download. For employees falling into this trap, there’s not even a single downside for such downloads; they find some apps useful on Play Store and download them directly to company’s phones, laptops, or tablets; without even realizing any security risks or complications of such unsanctioned apps. Without any departmental uniformity & technical compatibility, offices have become mere siloes of productivity, where teams are not able to share files; they are not able to collaborate effectively in rightful ways, or even worse. If any department needs some storage space, they might use public cloud and all of a sudden, the expense goes up. Just with one swipe of credit card, they can germinate issues for the IT team. From data breaches, to unplanned resources, to accidental shutdowns of the network because IT team was not ready for this information surge, Shadow IT policy has many devastating effects.
Uncover Shadow IT
“Have you ever used DropBox to send large documents or official files?”
Yes, then you have gone through the practicality of Shadow IT. Basically, Shadow IT is the set of those cloud-based applications that are not approved by your IT department, yet an employee can use them for various reasons (like quick service, etc). Various surveys have confirmed this fact that most of the employees use various blacklisted applications to get their work done, keeping safety and data confidentiality at stake.
The unmonitored and unauthorized data that flows from your business is never good for security. More challenges with uncovering shadow IT causes more danger in the scope of an organization. Installation of any third party application by your employees unknowingly causes high-risk malicious attacks like Phishing attack, Ransomware attack which puts your confidential data at a high risk.
Many times, employees are unaware of the risks associated with the use of unapproved applications for data transfer. These apps just wanted to use the shortest route to get their tasks done. It’s a job of the organization to make their employees aware of the effectiveness of cloud applications on resources by the organization’s IT department. There should be some system or tool to deny highrisk application usage on various or all employees’ devices.
Where can you find such type of a solution to monitor employee devices? How can you implement security checks on their devices, be it official approved laptops or Smartphones or their personal devices under BYOD (Bring your own device) policy? This can be procured by some policies or restrictions applied by an IT department of organization.
- Evaluate the requirement about particular software which is requested by an employee.
- Understand the necessity or urgency of requested software.
- Understand the risk of data leakage or data breach if haphazardly done for any third party application.
This analysis helps to evaluate the employee’s’ activities by setting up various policies within an organization. These policies should be within a scope of scrutinizing the requested tool by all means of security before enabling it.
Shadow IT Examples
Shadow IT emerged with the blast in advances cloud-based applications. This application blast permitted representatives to access IT arrangements through a web interface. Furthermore, with so much assortment, representatives could purchase a whole set-up of apparatuses with little no association from the IT division. To put it plainly, the interest for change was more reliable and quicker than the IT group’s assets, and even their mindfulness. Innovation had gone to the majority, and they needed to utilize that innovation. Presently.
In any case, accusing everything of the IT division isn’t reasonable and nor is it precise. Another primary reason for shadow IT risks is misalignment inside the business. An absence of control on the IT estate will, in general, make distinguishing an only explanation behind shadow IT solution. It implies the reason for shadow IT security can differ from business to business.
Few Disadvantages of Shadow IT
- Security lapse- IT offices frequently partner the utilization of shadow IT with an absence of cybersecurity — and all things considered. As anybody associated with cybersecurity dynamic can verify, keeping up business arrange security is intricate and costly. Shadow IT makes unmonitored, unstable pockets of information sharing and detailing inside an association, which can put restrictive information and critical resources in danger and slips by with consistency.
- Continuity issues- IT groups select and authorize specific frameworks with a unique regard for interoperability with other inside projects. While workers might be utilizing shadow IT frameworks since they can deal with discrete errands well, that doesn’t imply that they’ll be perfect with other center applications. Regardless of whether shadow IT can assist representatives with one an aspect of their responsibilities, that proficiency can be discredited on the off chance that they run into issues porting their work elsewhere.
- Highly expensive- Cybersecurity issues brought about by shadow IT can be fantastically costly for associations. A significant part of the profitability increases from permitting workers to utilize unsanctioned administrations that can be immediately nullified in case of a security break. Inside tasks could be influenced, and client connections could be irreversibly harmed.
3 Major Negatives of Shadow IT
- It is very costly
- It can compromise cloud security
- It usually goes against the processes
Shadow IT and CASB
CASBs identify cloud utilization utilizing firewall and intermediary logs since they keep up definite and forward-thinking vaults of all cloud administrations. Most CASB arrangements likewise permit organizations to survey the danger of any cloud administration by giving a hazard score determined to utilize more than 50 characteristics and over 260 sub-properties. This assessment IT security groups perform previously permitting cloud administrations is significantly quickened when using a library with exceptional cloud insight.
The responsibility for transferring to the cloud is a significant hazard evaluation model since it represents a threat to the introduction of touchy information. For instance, some PDF change administrations incorporate administration terms that guarantee responsibility for documents transferred to their foundation. It spots critical corporate information in danger if a worker is uninformed of the threats related to the administration they are utilizing to be progressively beneficial.
When each cloud administration is assessed, IT groups can utilize the hazard evaluation rating gave by the CASB answer to characterize adequate cloud administration strategies. The Cloud Access Security Brokers, at that point, incorporates with the venture’s current firewall or secure web entryway to implement approaches. This ability is pivotal for dealing with an association’s shadow IT weaknesses since it can conceivably boycott risky administrations and advance important ones, restricting information weaknesses and augmenting representative efficiency.

